Your guests might include Uncle Charlie, who has brought down the networks of entire companies with his passion for double-clicking on any email attachment, or perhaps it is your niece Sara, who can never say no to an ActiveX installation. As we all know, computer networks are the most vulnerable from within. This article contains technical and social tips on effective home network security.
Planning
The first step in preparing any defense is planning. First you have to analyze the capability of the potential threat, and the duration of their stay, though estimating duration may be difficult. I once had a colleague who welcomed a cousin into their place. The cousin had just finished a B.S. degree and was looking for a job in the area. After 5 months, my colleague realized the job hunt strategy was the following daily practice:
- Wake up around noon and devour all available cereal products and juices.
- Queue up 150 files for Kazaa downloads.
- Take a leisurely bubble bath.
- Devour all available microwavable food items.
- Perform web browsing of non-job related web sites clicking “OK” and “YES” in response to any question.
- Rewire home entertainment system to play downloaded MP3s and movies.
- Briefly search monster.com using search term “‘high paid’ and ‘entry level’ and ‘international travel required’”. 0 jobs found.
- Wait to devour all cooked food items that appear between 6pm and 9pm.
- IM other job seeking friends until 2AM while devouring any remaining food items that do not fall into the condiment and spice category.
Needless to say, this type of person needs the tightest crackdown available.
The Router As An Internal Defense Mechanism
Most of the current routers made for the home by manufacturers such as Linksys, DLink, and Siemens, now ship with many security features you can take advantage of. These features are included ostensibly to protect young children in your home from the adult areas of the internet, but when used effectively can protect the Internet from the adults in your home.
It is important you give your router administrator account a strong password. This prevents any technically well informed house guest from breaking into your router and reconfiguring the settings. Although brute force and dictionary attacks from blood relations are relatively rare, be wary of the “friend of a cousin” type. You might ask them to empty their pockets and do a quick search to make sure they have not brought any CDs (watch or those small, USB key chain drives) with cracking software onto the premises.
URL filtering is one possible defense mechanism. As shown below, a router with URL filtering will let you type in filter strings. If any part of a URL matches a filtering string, the router will block the request.
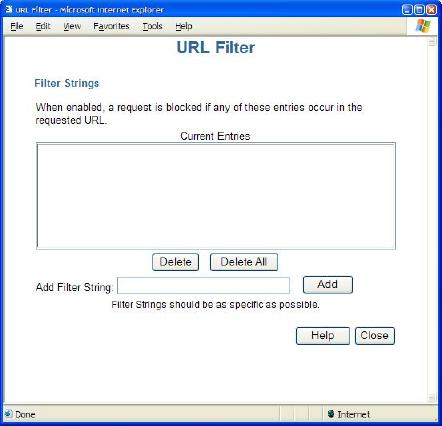
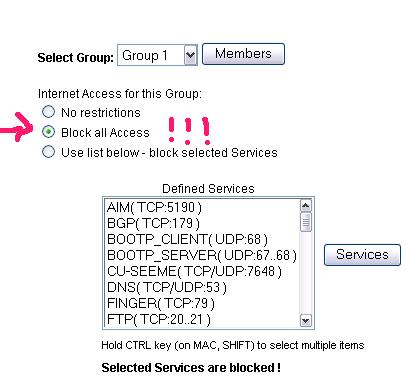
Many home routers also allow some form of port filtering. Port filtering will allow you to block some selected services. Some routers will ship with predefined services allowing you to simply check them off the list. If you have multiple PCs, you can offer your house guest the use of your least favorite computer, then use the router to block all access from this node (see figure below).
A Brief Word On Awkward Social Situations
At some point, your guest may approach you about the sudden lack of connectivity from your home, and point out how this is an inconvenience. You need to select from one of three strategies below. Practice the following mock conversations in front of a mirror for the best preparation.
The Direct Approach
The direct approach is best to use with long term guests. Any other technique will only result in additional nagging for connectivity.
Uncle Charlie: Say, your Internet thing doesn’t work.
You: You need to use the Internet thing?
Uncle Charlie: I’ve been trying to check stock quotes before the market opens tomorrow.
You: The last time you were on my desktop I had to take the hard drive to the county hospital’s MRI machine and have the disk wiped clean in a magnetic field. I don’t even want you to look at my programmable thermostat because I fear for the safety of my property.
Uncle Charlie: Do you get the Wall Street Journal?
The Techno-babble Approach
We also know this technique as “security through obscurity”. It works best on guests with less than a 7 day stay and little technical ability.
Uncle Charlie: Say, I’m having some problems getting to My Internet.
You: Oh I see. I think I know what the problem is.
Uncle Charlie: That’s great!
You: It will only take me a couple hours to reverse the polarity of my TCP/IP stack and grep out a couple bad hostnames. You want to watch?
Uncle Charlie: Well, ah, actually I was thinking of having some more egg nog and watching the Bloomberg channel.
You: Well, have a seat in the living room, I’ll bring the glasses in.
The Little White Lie Approach
This technique is best used when you do not want to hurt any feelings, and when the guests have less than a 3 night stay.
Uncle Charlie: Say, I think the Internet is broke here.
You: <Long sigh>. It must be the squirrels again.
Uncle Charlie: Squirrels?
You: Yes, remember last year about this time they came out looking to stock up nuts before the snow. Well, they run up and down the cable outside and make a mess of things. Does the phone in the kitchen still work?
Uncle Charlie: I haven’t tried to…
You: I guess I better check. If not I’ll call the cable company on my cell phone. They have really great customer service. They will probably come out and fix things up right after you leave in the morning.
Uncle Charlie: I’m impressed. Are they traded on the NYSE?
IE Lockdown
If you are running XP or a Windows Server product, give your house guests a separate login to the machine in question. Start IE and go to the Security tab of the options dialog. Set all zones to “High security”. Set the privacy slider to “High”. Disable any setting related to ActiveX and JavaScript.
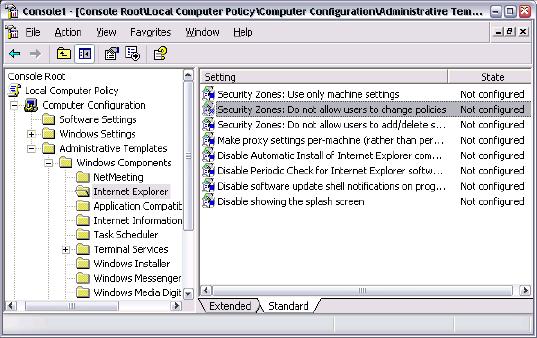
With the settings in place, log back into the machine as an administrator and start the Local Computer Policy MMC. As shown in the next figure, navigate to IE settings, and make sure “Do not allow users to change policies” is set to “enabled”. You can also prevent MSN messenger from running in this policy section.
When All Else Fails
It is extremely important to have yourself and other members of your household prepare for the “Code Red” scenario. The “Code Red” scenario means all other fail safes have been bypassed, and your home network and PCs are only keystrokes away from destruction. Find the circuit breaker for your house and make sure there is a clear path leading to the master “OFF” switch. Yes, a “Code Red” means you are shutting off all electrical flow to the household. If you let your guests use a laptop or a machine on a battery backed UPS, you’ll need to take additional steps beyond the scope of this article.
The most important step in “Code Red” execution is to have a code phrase. When any member of the house hears “the code phrase” used in conversation, they should know it is time to leap into action and head straight to the kill switch. Naturally, you must make sure the code phrase is a rare saying that would not normally be used in the typical flow of conversation in your household. As an example, we will use the code phrase "Ich bin ein Berliner" in the following conversation.
Niece Sara: Oooh. My friend sent me a Johnny Depp screen saver. Can I install it?
You: Um, actually…
Uncle Charlie: Sara, I said you could only use the computer here for homework assignments. Now let Uncle Charlie in to check his email.
You: “ICH BIN EIN BERLINR!!! ICH BIN EIN BERLINER!!!”
Uncle Charlie: Is that German? I didn’t know you spoke German.
<scamper of feet in basement>
You: Well, I’ve been listening to these language tapes during the commute and...
<total blackout>
Uncle Charlie: What happened!?
You: <sigh> The squirrels must have hit the transformer again.
Uncle Charlie: I’d say you have a serious squirrel problem around here. This happened last year too. Are they rabid? Maybe you should call the SPCA.
You: I'm not postive I can ensure your safety here. How about if I drive you to the Hampton Inn downtown?
Conclusion
Entertaining out of town guests should be an enjoyable time, so don’t let computer problems get you down. We have covered many basics in this article, but remember with guests, the only safe computer is a computer without power.



 Twitter
Twitter
 Search
Search
 About
About
 Learn C#
Learn C#